Photo by Oleg Didenko on Unsplash
You are using a version control system and your project uses some services that require API keys. Everything is all good and well when it is on your local machine, but you obviously don’t want to share these API keys with the world.
How can we still preserve our API keys within our application, but also hide them when we upload our code to our repository?
We want to be able to still use our API keys in a normal fashion inside our applications, but also not expose them.
That’s where secrets come in. Similar to those that you keep only to yourself, but in a developer kind of way.
Secrets can represent crucial information that is required by your application to operate, but should not be visible to anyone working outside the project. These can be API keys or authorization tokens, but in essence it is any piece of authorization information that should only be used by you and you alone. Similar to how you don’t want to share your password to a website with anyone else.
🚨 Disclaimer: Be aware that the solution provided in this article works for not exposing your secrets from your version control system, but since they are part of your application, they can still be discovered by decompiling your APK. To find out how to do that, here is a good starting point.
Keeping Your Secrets Safe
- In your project, you should have a local.properties file under the root directory of your project
- To make sure it is ignored by your version control system, open the .gitignore file and see it is found there:
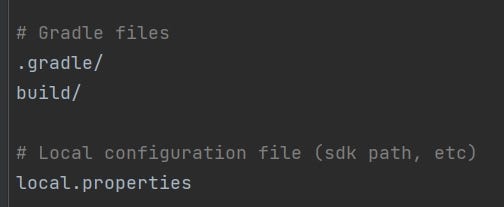
Part of .gitignore file
3. You will need to import to your project the Secrets Gradle plugin:
3.1. Go to your project’s root build.gradle file and paste in the following line:
buildscript {
dependencies {
id 'com.google.android.libraries.mapsplatform.secrets-gradle-plugin' version '2.0.1' apply false
}
}
Job Offers
3.2. Go to your app’s build.gradle file and paste in the following line:
plugins {
...
id 'com.google.android.libraries.mapsplatform.secrets-gradle-plugin'
}
4. Add your API key inside the local.properties file:

local.properties
5. You can use your secret inside your AndroidManifest.xml file by adding a meta-data tag inside your application tag:
<application
android:allowBackup="true"
.....
>
<activity>
....
</activity>
<meta-data
android:name="YOUR_API_KEY_NAME" /// Choose any value here
android:value="${API_KEY_NAME}"/> /// Write the name you gave inside your local.properties file
</application>
6. To access your API key, you can use the PackageManager to get the meta data:
val applicationInfo: ApplicationInfo = application.packageManager
.getApplicationInfo(application.packageName, PackageManager.GET_META_DATA)
val apiKey = applicationInfo.metaData["YOUR_API_KEY_NAME"]
7. Alternatively, you can also use the BuildConfig object to get it:
BuildConfig.YOUR_API_KEY_NAME
That’s it. Now you can rest easy knowing that your secrets won’t be exposed by your version control system.
Enjoy keeping your secrets ㊙️
I used this on one of my recent projects, and you can see the source code (sans the secrets) here:
GitHub – TomerPacific/movies-presenter
And if you want to check out other articles that I have written, you can go here:
This article was originally published on proandroiddev.com on January 15, 2023








